Tech Solutions That Transform Africa
Where Innovation Meets Impact
Tailored Cloud, AI, and Software Solutions Driving Change in Education, Energy, and Finance

Core Services

Reliable Digital Infrastructure:
Cybersecurity Solutions
Protect your organization from cyber threats with our comprehensive cybersecurity services. We ensure your systems, data, and digital operations are safe, compliant, and resilient.
Secure, Scalable Cloud Solutions:
We help organizations move to the cloud -- for the right reason -- or optimize their existing cloud setups on platforms like AWS and Azure. This means you get flexible, reliable, and cost-effective digital operations without managing physical servers.

Custom Software Development
Our team creates and delivers software tailored to your specific needs, ensuring it’s user-friendly, efficient, and scalable for future growth.

AI Strategy and Implementation
We guide you in adopting and adapting AI technologies, helping you automate processes and make data-driven decisions that lead to real-world impact.
Education Solutions Transform learning landscapes across Africa
Energy Solutions Powering Africa's sustainable future
Financial Solutions Innovate and democratize financial services
- Mobile Banking Platforms Secure, user-friendly solutions bringing financial services to underserved areas
- AI-Driven Risk Assessment Enable financial institutions to serve broader markets with confidence
- Blockchain-Based Transaction Systems Ensure transparent, efficient, and secure financial operations
- Financial Inclusion APIs Connect traditional banking with innovative fintech solutions

Custom Solutions
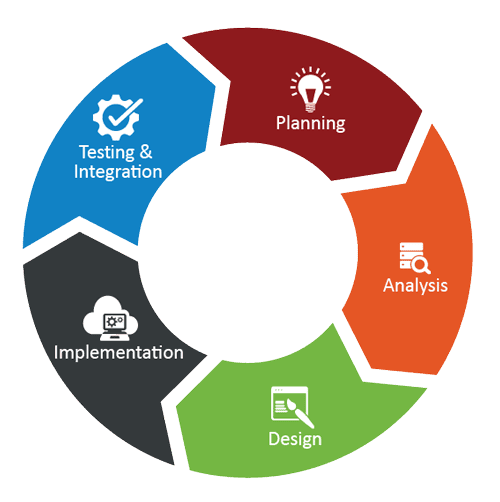
Our Approach
Why Choose Canvas • Africa
Read What Our Clients Say

Canvas • Africa didn't just provide a solution; they transformed how we operate, enabling us to serve our community better than ever before.
Managing Director at Cablenet Electrical South Africa

We partnered with Canvas Africa for cloud platform engineering services on a critical client project. They impressed us with their expertise and ability to deliver results efficiently. Their collaborative approach ensured seamless integration and a successful outcome. Canvas Africa is a reliable and skilled technology partner we highly recommend.
CEO at Nanyata Siyaya Holdings South Africa

